Stubby Manager GUI
Latest release is 0.4.0-a2 (11-Dec 2020)
Background
The Stubby Manager project is designed to provide a Graphical User Interface to manage Stubby aimed at both non-technical and advanced users. It will initially be supported on Windows only, macOS support will be added later.
dnsprivacy.org is grateful to the Comcast Innovation Fund for supporting this project.
Status
The code is still in development, an alpha release is available for early testing. Feedback is welcomed but note that the alpha release is not quite feature complete. Outstanding work items for the beta release include:
- Detection and use of network resolvers so the Trusted profile can use them
- Add, Filter and IPv6 options on the server table
- Adding a ‘None’ option to the Network drop down
- Various usability improvements including improved alerting, icons and tooltips.
Installation
The Windows Installer can be obtained from this page Latest windows installers
After installing and running we recommend making the Stubby Manager Icon permanently visible in the system tray (select the Start menu and type ‘select which icons appear on the taskbar’).
You may also want to manually configure the Stubby Manager application to start at login/wake - this can be done
- Manually by creating a desktop short cut for the Stubby Manager application and then copy/pasting it into the %appdata%\Microsoft\Windows\Start Menu\Programs\Start-up directory
- Installing a scheduled task based on the C:\Program Files\Stubby\StubbyManager.xml file.
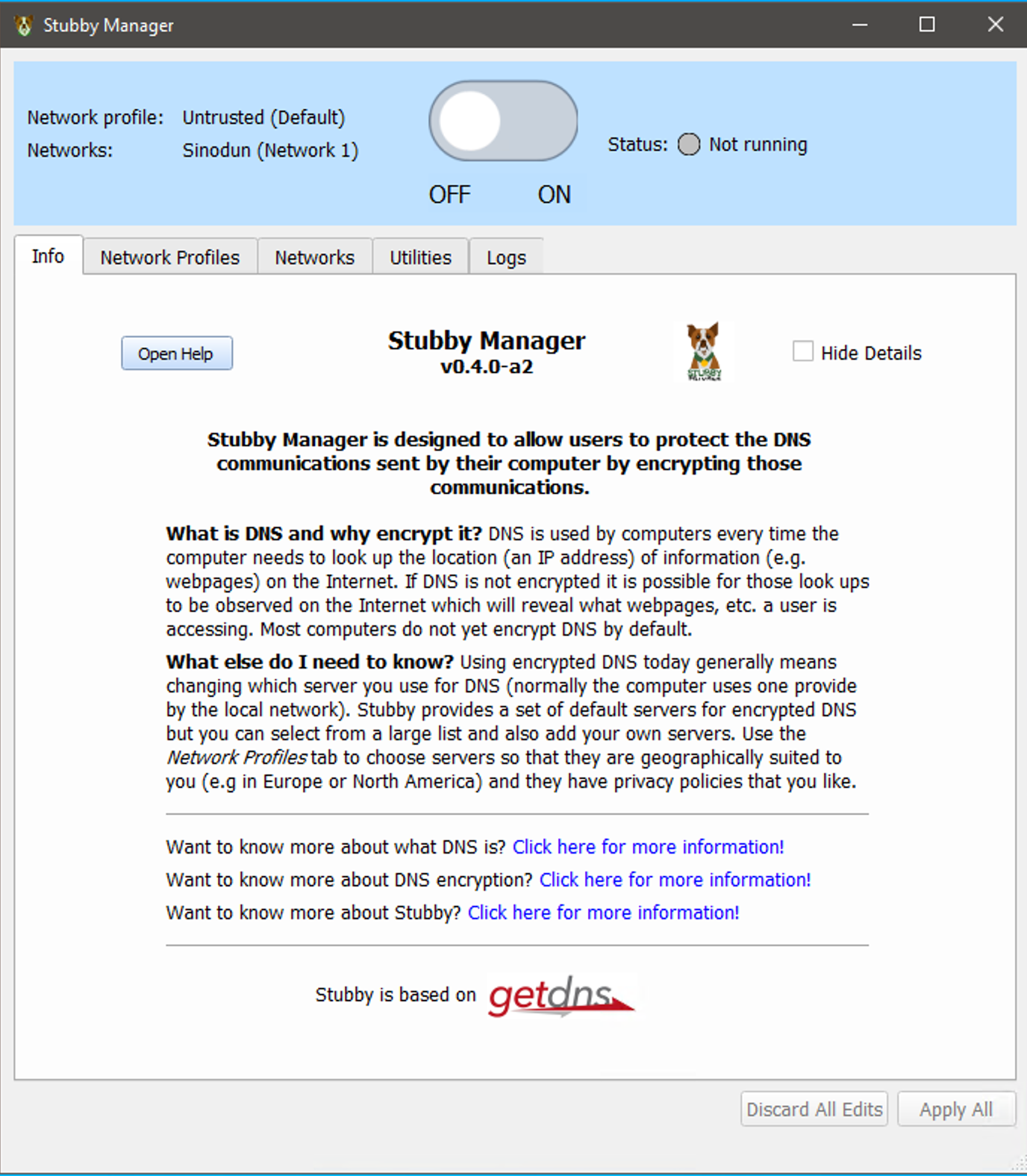
Overview
Welcome page
The ‘Info’ Tab provides background information and more details on DNS, DNS encryption and getdns/stubby. These details can be hidden to provide a cleaner interface.
On/Off button
For users who are happy to simply use the defaults provided (including the Stubby maintained resolvers) then simply hit the big button to turn Stubby on! Stubby will then automatically start again if the machine is rebooted. The display shows which networks and which network profiles are in use (see below)
Network Profiles
Three profiles are provided for flexible configuration for users who want to customise their setup. Each contains options to set the following:
- Encrypt DNS - Use only TLS as a transport (otherwise UDP, TCP and TLS are all available)
- Always Authenticate - Only connect to servers that have authentication information and where the TLS handshake can verify that information.
- Validate data - enable stub mode DNSSEC validation
- Round Robin - open connections to all the selected servers and send queries in turn to each. Default is to use the selected servers in order unless they become unavailable.
Untrusted
This is the default profile provided on install, it encrypted DNS using DNS-over-TLS (DoT) to the Stubby recursive resolvers. It is suitable for use in most networks where DoT is not blocked - note however that the resolvers are based in Europe so users outside Europe may want to choose alternative resolvers for better latency.
Trusted
The trusted profile currently uses the Quad9 resolvers BUT in the beta release will use the network provided resolvers for resolution, attempting to use DoT opportunistically. In effect this means that connections will be encrypted if the network resolver supports DoT, but not (at this point in time) authenticated. If the network resolver does not support DoT, clear text (UDP/TCP on port 53) will be used.
Hostile
This is appropriate for use in networks with stricter security policies or that attempt to engage in active surveillance of users e.g. by blocking DoT or well known DoH resolvers. In the beta release it will use DoT to the Quad9 resolvers, in a future release it will support fallback to DoH to the Quad9 resolvers. Note that it may be better to use a full VPN on such networks.
Networks
Users can configure a default profile to be used automatically when joining new networks and also specific profiles to use on specific networks on this tab.
Utilities
This tab provides more detailed logging and control for troubleshooting or advanced users.
Logs
The beta release supports displaying the logs from the stubby deamon in this tab, a future release will allow inspection of DNS queries. (Since stubby runs as a daemon, advanced users can use tcpdump or wireshark to inspect their DNS queries listening on local host port 53).
Code
The code is available on github: https://github.com/Sinodun/Stubby_Manager
Bug reports and feature requests
Please file issues at: https://github.com/Sinodun/Stubby_Manager/issues
Future features
Future release will include a probe mode that can be run to determine the connectivity and latency of available resolvers and also some of their basic (measurable) properties such as DNSSEC support.
A custom profile and expert mode will also be available to further customise the Stubby configuration.